In this blog, I will discuss how to authenticate your database instance using AWS Identity and Access Management (IAM) database authentication. In keeping with AWS’s best practices of “shared responsibility,” the AWS IAM service is a “customer responsibility” layer of security for your data.
Using AWS IAM with Amazon Relational Database Service (Amazon RDS)
You should create an individual IAM user for each person in your organization who manages Amazon RDS resources. An IAM user can sign into the AWS Management Console for interactive tasks and make programmatic requests to AWS services using the API or CLI. In many cases, you can take advantage of IAM roles and their temporary security credentials instead of using the long-term credentials associated with an IAM user. An IAM user can temporarily assume a role to take on different permissions for a specific task.
IAM policies enable you to manage permissions to your workforce and systems to ensure least-privilege permissions. To grant permissions to IAM roles, attach a policy that specifies the type of access, the actions that can be performed, and the resources on which the actions can be performed. IAM enforces those permissions for every request. Access is denied by default and is only granted when permissions specify an “Allow.”
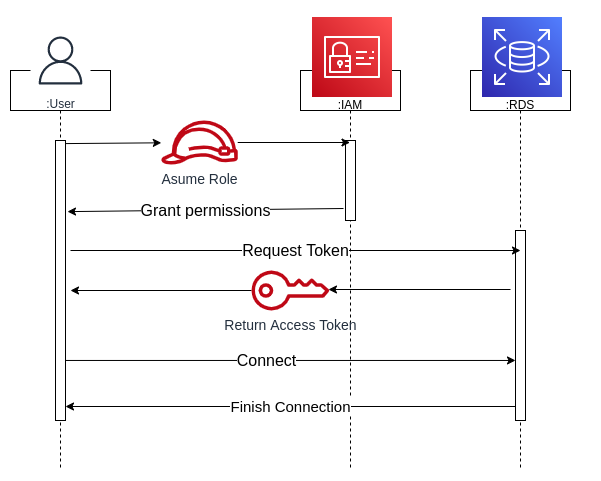
Identity and access management (IAM) is a collective term that covers products, processes, and policies used to manage user identities and regulate user access within an organization. This feature is available for databases when using MySQL and PostgreSQL engines. Below is a sequence diagram of how IAM works.
Amazon RDS is a fully managed relational database. As such, AWS is responsible for managing the underlying infrastructure and foundation services, operating system, database setup, and patching and backups. AWS customers, however, are responsible for protecting the data stored in databases (through encryption and IAM access control), managing the database settings that are specific to the application, building the relational schema, and network traffic protection. Therefore, it is essential to understand when to use IAM and how to apply it.
Tutorial on how to perform AWS IAM database authentication
In the tutorial video below, I am a user who assumes a role. I have the correct permissions to access IAM database authentication. I am granted the permissions and request an authentication token, a string of characters created by Amazon RDS that is used instead of a password by the database user. Therefore, I will not have to store any passwords on the database. I will need to use this token every time I access the database. It’s important to remember that this login only lives for 15 minutes because, after 15 minutes, Amazon RDS returns the access token and I’ll need to start again.
For the detailed step-by-step tutorial, please view the video below.
Need help with data and analytics? We’ve got the experience, AWS data and analytics knowledge and credentials, plus our research initiatives, to help you plan and execute your strategy.


