As our clients build and deploy workloads on AWS, they often use a multi-account strategy. Multiple AWS accounts serve as a resource container to segregate workloads for rapid innovation, simplified billing, flexible security controls, and to meet the needs of business processes.
You may already be familiar with using AWS Organizations for a multi-account structure. So, why should you consider using AWS Control Tower? While AWS Organizations enables you to manage your environment across multiple accounts centrally, AWS Control Tower automates many of the steps required to build your environment and govern at scale. It simplifies many of the provisioning steps for other AWS services, saving time and effort by providing a cloud-ready governance model.
Terminology
Landing Zone: The overall multi-account environment that Control Tower sets up.
Guardrails: Automated implementation of policy controls focusing on security, compliance, and cost management.
Blueprints: Well-architected design patterns used to set up a Landing Zone.
Organization Unit (OU): An entity created within your organization to group accounts for governance.
Account Factory: Provisions new accounts and enrolls existing accounts.
Use cases
Private sector. If your organization has many teams or regional offices across the globe, with AWS Control Tower you can manage multiple AWS accounts easily on a single dashboard. Integrate accounts and link them to AWS services so that they function as a single entity program.
Public sector. Government, education, and healthcare organizations are particularly concerned about control/governance, security, and regulatory compliance. AWS Control Tower has built-in governance and best practices and provides visibility into compliance status quickly.
How AWS Control Tower works
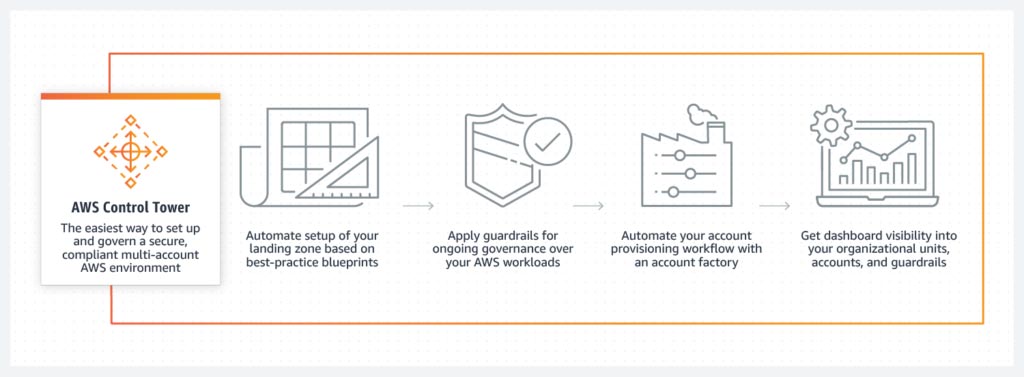
Source: AWS Control Tower. Amazon Web Services.
https://aws.amazon.com/controltower/?control-blogs.sort-by=item.additionalFields.createdDate&control-blogs.sort-order=desc
Control Tower provides:
- Governance of all sub-accounts.
- Account Factory, where you can provision new accounts and enroll existing accounts.
- Logging and audit trails.
- Centralized billing.
- A management dashboard.
- User management.
AWS Control Tower creates an automated landing zone using AWS Organizations. Administrators can set up a new multi-account environment with just a single click in the AWS Management Console.
Organization Units (OUs) group accounts for governance. OUs have guardrails enabling AWS Control Tower to implement preventive or detective controls to govern resources and monitor compliance across groups of AWS accounts. Each guardrail enforces a single rule.
There are three ways to provision new accounts in the AWS Control Tower landing zone:
- Account Factory console that is part of AWS Service Catalog.
- Enroll account feature within AWS Control Tower.
- AWS Control Tower landing zone’s management account, using Lambda code and appropriate IAM roles.
Deploying AWS Control Tower
When you deploy AWS Control Tower, it creates three accounts: a management account, audit account, and log archive account.
- Management account — a shared account that’s used for billing, Account Factory provisioning of accounts, and managing OUs and guardrails.
- Security OU with two shared accounts
- Audit account — a restricted account that provides security and compliance teams with read and write access to all accounts in the AWS Landing Zone. (Note: It does not allow you to log in to other accounts manually.)
- Log archive account — a repository for logs of API activities and resource configurations from all accounts in the AWS Landing Zone.
The architecture diagram below is for an organization with multiple projects comprising multiple teams. There are three OUs in addition to the management account, audit account, and log archive account:
- Sandbox OU — for code testing in software development environments.
- Two project OUs: Project 1 and Project 2. Teams have dedicated AWS accounts within each project OU.
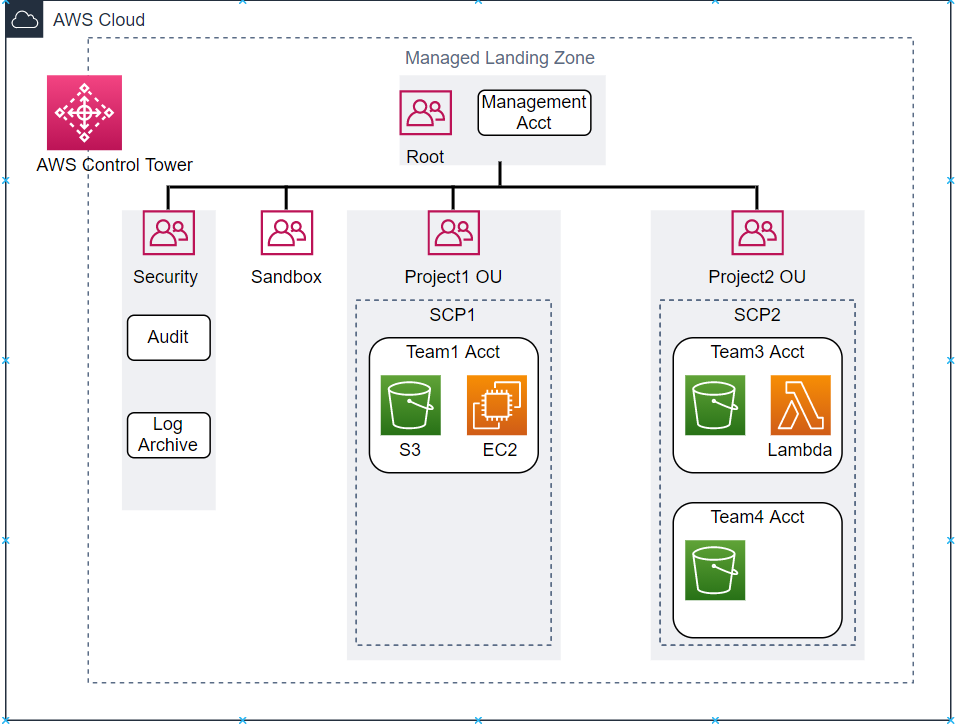
Source: Balasubramanyan, M. (2021, May 19). Fast and Secure Account Governance with Customizations for AWS Control Tower. AWS Architecture Blog. https://aws.amazon.com/blogs/architecture/fast-and-secure-account-governance-with-customizations-for-aws-control-tower/
Customizing AWS Control Tower
Customizations for AWS Control Tower enable you to include additional accounts or OUs in the managed landing zone, combine it with other AWS services, and deploy resources and governance at scale. To do so, use a custom AWS CloudFormation template and service control policies (SCPs) deployed to individual accounts and OUs.
In the architecture diagram below, code is uploaded to Amazon Simple Storage Service (Amazon S3) or any central repository, and AWS Control Tower triggers an Amazon EventBridge event rule. Use Amazon Simple Queue System (Amazon SQS) with AWS Lambda. Lambda polls the queue and invokes a Lambda function synchronously with an event that contains a queue message. It triggers the AWS CodePipeline workflow, which automatically initiates a series of stages (e.g., build, test, and deploy). Each stage is made up of a sequence of actions, such as building code or deploying to test environments
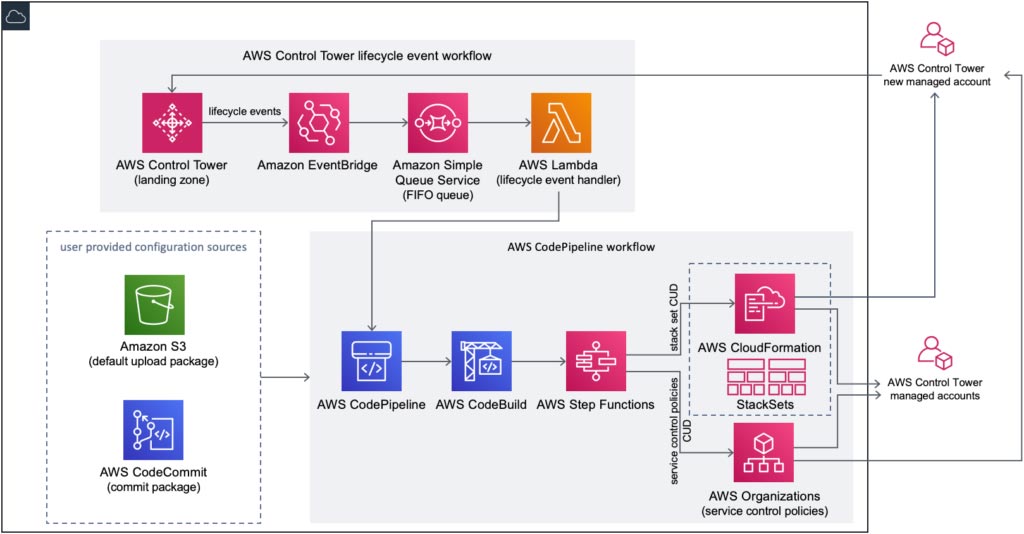
Source: Customizations for AWS Control Tower. Amazon Web Services – AWS Solutions Library – AWS Solutions Implementations. https://aws.amazon.com/solutions/implementations/customizations-for-aws-control-tower/
One of the actions that AWS CodePipeline performs is deploying AWS CloudFormation StackSets as part of the CI/CD process. It creates stacks in AWS accounts across AWS Regions by using a single AWS CloudFormation template. All the resources included in each stack are defined by the stack set’s AWS CloudFormation template, where you specify CPU options for your account.
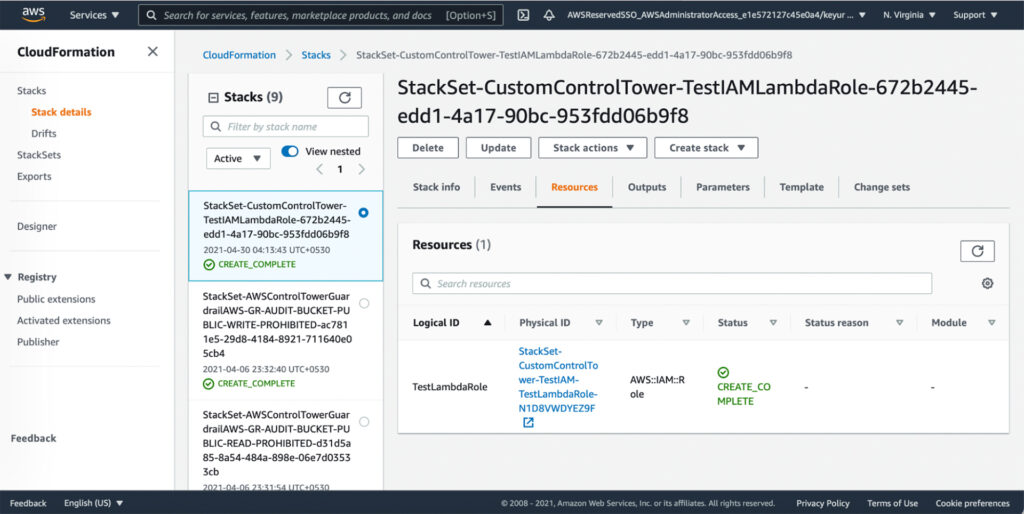
To check the customization progress on AWS CodePipeline, navigate to the AWS CodePipeline Console on the AWS Control Tower Management account. Select Custom-Control-Tower-CodePipeline to track the status of the pipeline at various stages, and wait about 10 minutes until the last stage CloudformationResource is complete.
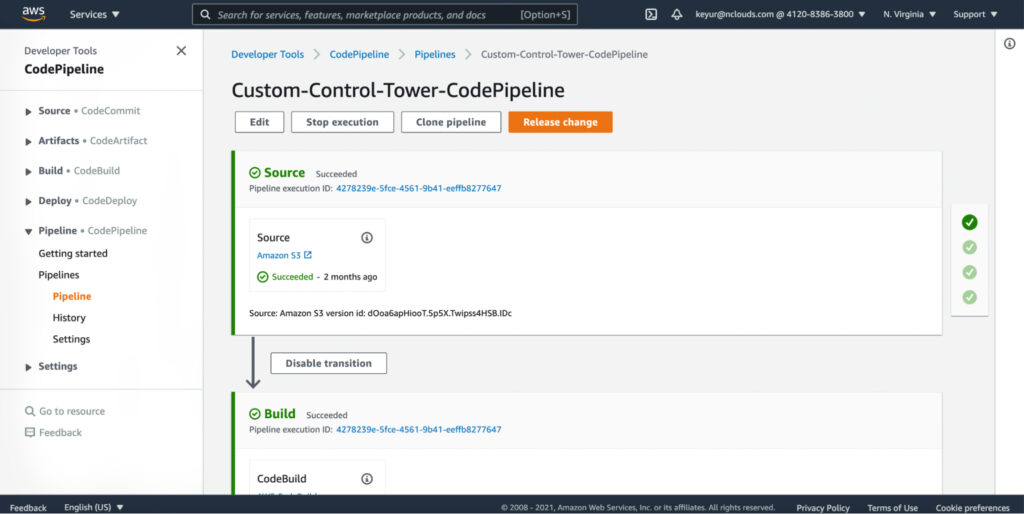
Setting up the landing zone for an existing AWS Organization
Setting up the landing zone in AWS Control Tower takes an hour or more to complete, depending on the size of your existing AWS Organization and the number of accounts it contains. The accounts in AWS Control Tower — and the billing for them — become part of your existing AWS Organization.
Once AWS Control Tower is set up, it provides a dashboard indicating the status of the AWS Control Tower environment. The organizational units screen of the dashboard shows the registered OUs, including both the new OUs created by AWS Control Tower and the existing OUs. It also shows the registered accounts in the OUs. Accounts governed by AWS Control Tower are shown as “Enrolled.”
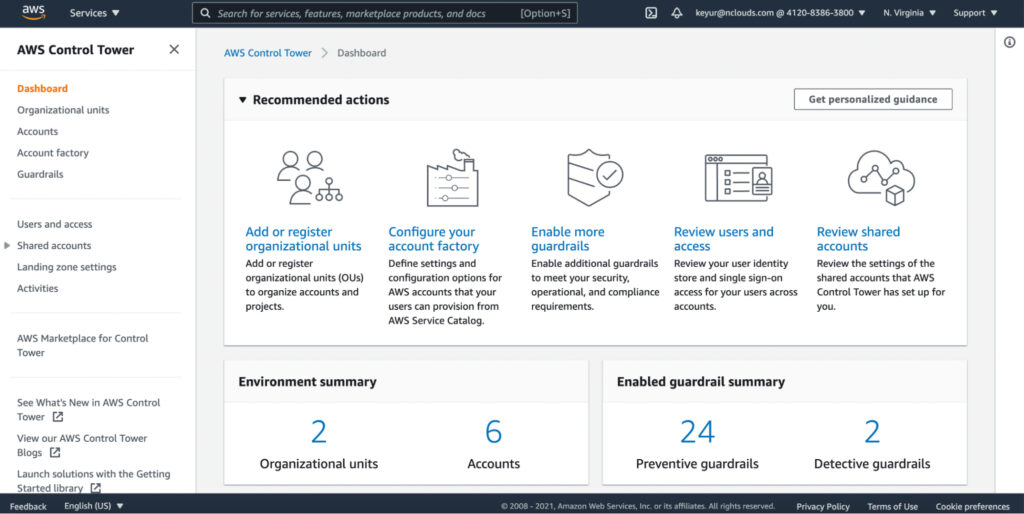
If you want to add a new account, click on “Enroll account” in the AWS Account Factory screen.
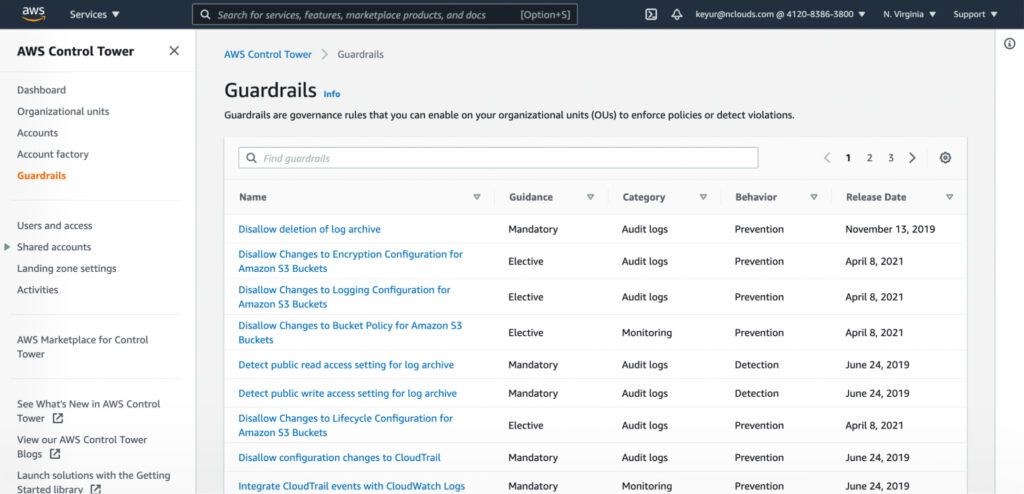
To set up guardrails — governance rules enabled on your OUs to enforce policies or detect violations — go to the Guardrails screen of the dashboard.
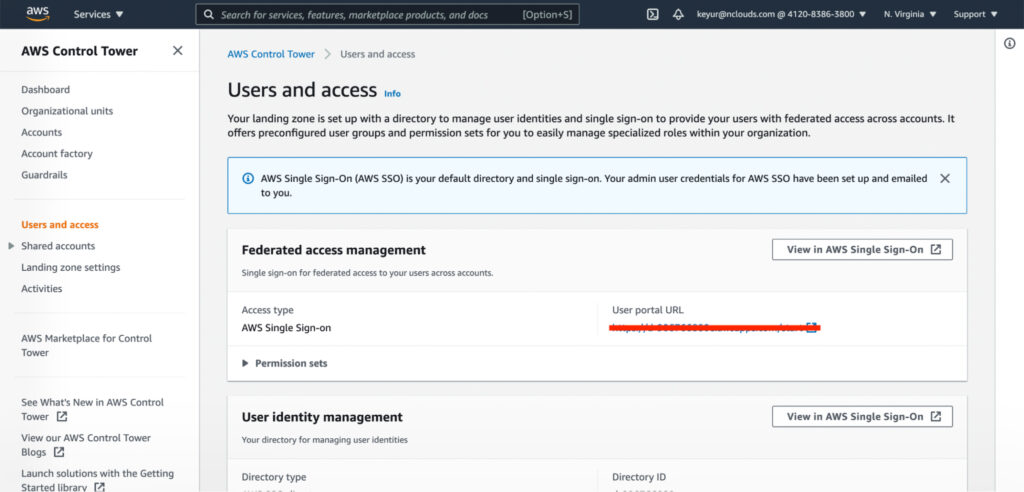
As shown on the users and access screen of the dashboard, the landing zone is set up with a directory to manage user identities and single sign-on. It provides users with federated access across accounts. To manage specialized roles within your organization, use the preconfigured user groups and permission sets.
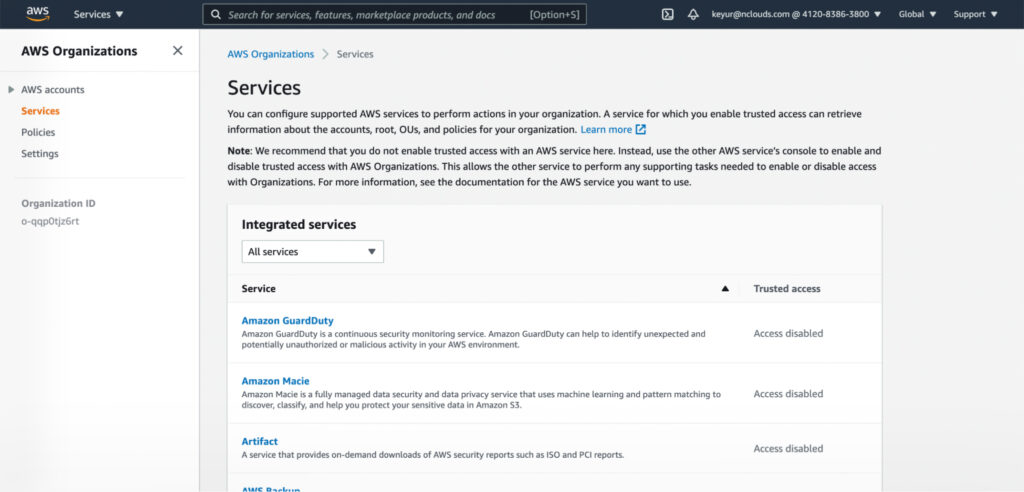
Integrating AWS services with AWS Organizations
While you can use the AWS Organizations Console to configure supported AWS services to perform actions in your organization, AWS recommends that you use the other AWS service’s console instead. Doing so enables that service to perform supporting tasks required to enable/disable access with Organizations.
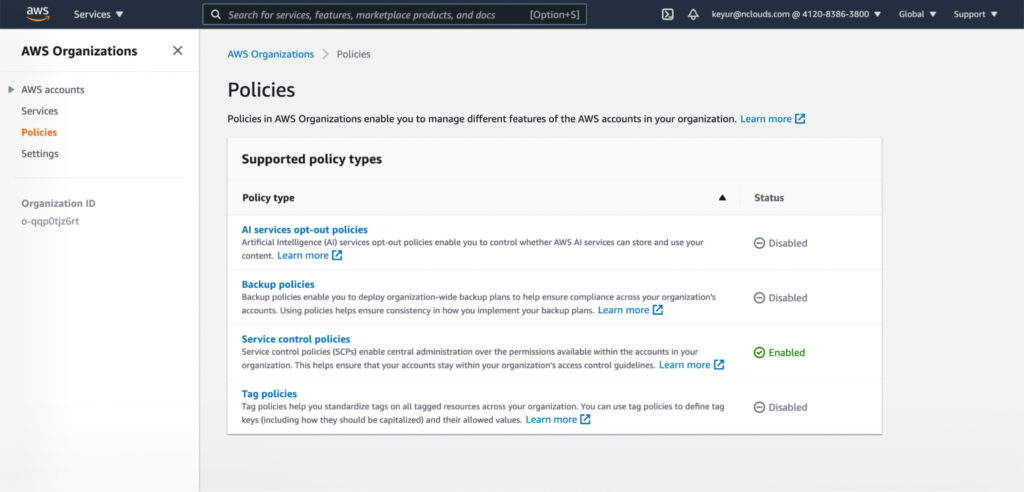
Setting AWS Organizations policies
The Policies page in the AWS Organizations console shows supported policy types and whether they are enabled or disabled. To enable a policy type, sign in to the AWS Organizations console as an IAM user or assume an IAM role. On the Policies page, choose the name of the policy type that you want to enable and select Enable policy type. Then the page is replaced by a list of the available policies of the specified type.
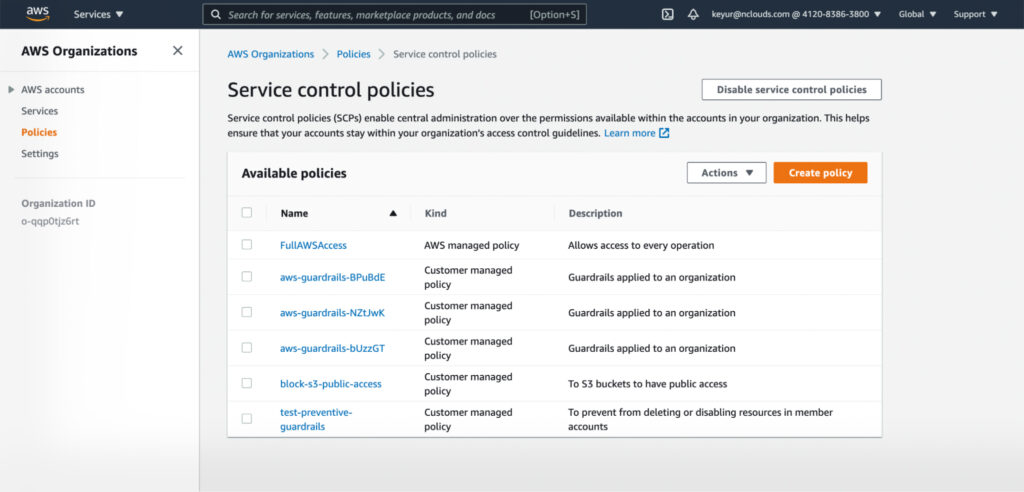
Select Service control policies on that page to set SCP rules, which brings up the Service Control Policies page.
For more information on AWS Organizations, read our blog, “How to Achieve Fine-Grained Control with AWS Organizations.”
Do you need help with your multi-account strategy on AWS? Connect with the nClouds team — we can help with all your DevOps and AWS infrastructure requirements. Contact us.


