Case Study
nClouds AWS Case Study | Superside
Superside is a VC-backed (Y-Combinator) always-on company that supplies marketing and sales design, at scale, to enterprise teams. Benefiting from the gig economy, Superside provides its clients with a dedicated team of pre-screened freelance designers via a design subscription service. Superside’s platform enables design collaboration, and it delivers reliable and fast (12-hour) turnarounds at one-third the typical agency cost. To learn more, go to www.superside.com.

Industry
Location
The Challenge
Featured Services
Improved performance efficiency
Enhanced security
Optimized costs
CHALLENGE
“We were impressed with nClouds’ recommended architecture for a unified deployment platform. They truly became an extension of Superside’s team as we implemented the migration.”
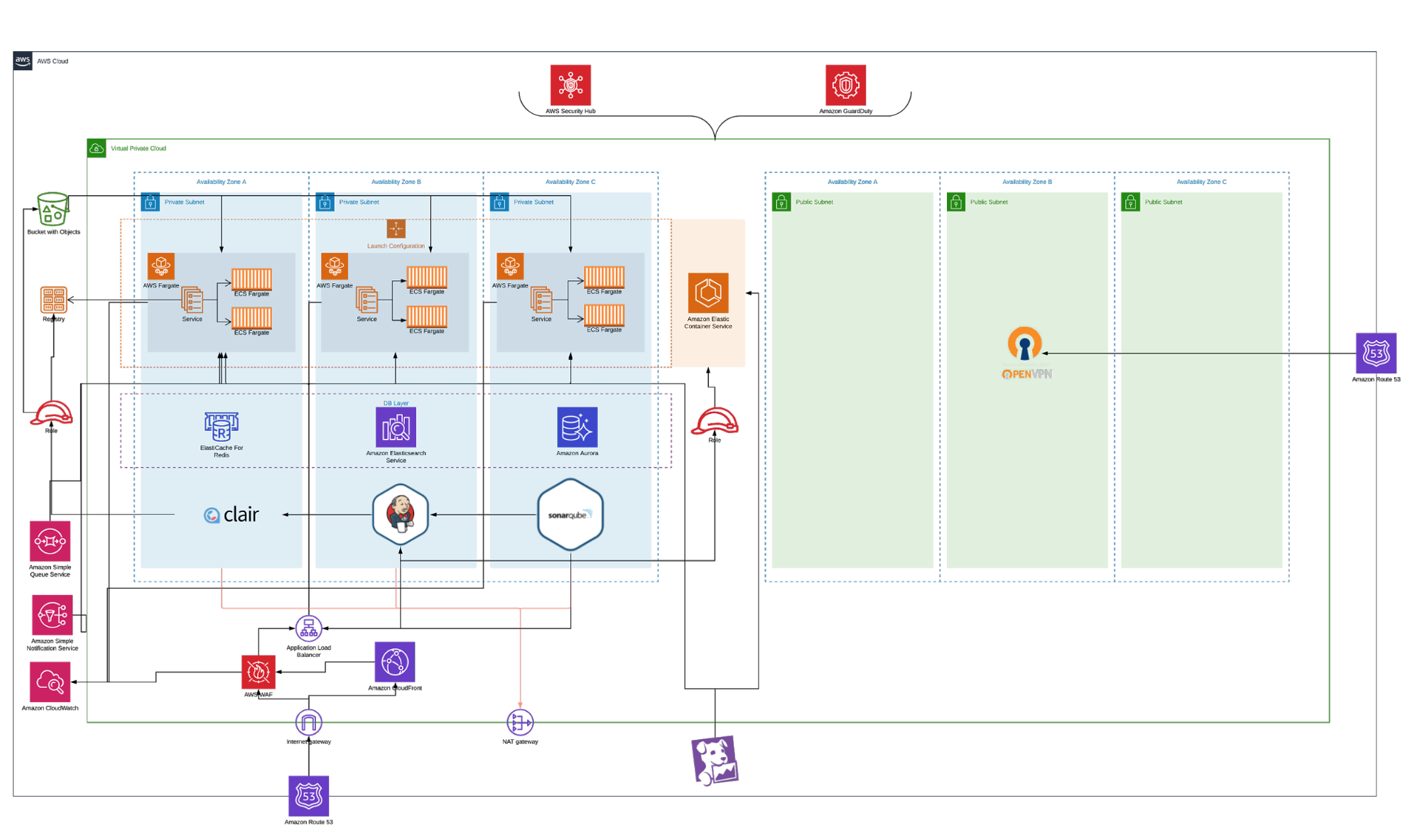
THE SOLUTION
Superside wanted a unified deployment platform to provide improved performance efficiency, enhanced security, and optimized costs for their compute workload.
Superside’s existing workload had services running in AWS Elastic Beanstalk (in multi-container Docker mode), and Amazon Elastic Container Service (Amazon ECS). nClouds used HashiCorp Terraform to build the infrastructure to support apps in a serverless environment using AWS Fargate on Amazon ECS, and built a CI/CD pipeline for these services in Jenkins (replacing Atlassian Bamboo). The new Amazon ECS cluster has multi-zone availability, AWS Auto Scaling policies, and integration with AWS Systems Manager Parameter Store.
Ready to Accelerate?
No matter where you are in your cloud journey, we can help you migrate, modernize, and manage your AWS environment. Let’s accelerate your growth and fast-track your business outcomes.
