Security is a big concern for web applications, especially when they’re used globally. When an asset is public, it’s prone to different kinds of attacks from different hackers. Unfortunately, sometimes developers or organizations don’t focus on securing their web apps from common exploits, or they invest so much time and resource in security that product functionality suffers.
Common types of web attack
There are many types of web attacks, but the most common are distributed denial of service (DDoS), SQL injection, and cross-site scripting (XSS). I’ll address some solutions to these in this blog post.
AWS Web Application Firewall can help
AWS Web Application Firewall (AWS WAF) helps to protect your web applications from common exploits that can affect application availability, breach security in your application, and affect application performance.
- Worried about building security around common attacks? AWS WAF is a solution for this.
- How about blocking a certain IP address from hitting your site? There is no easy way to block it without AWS WAF.
Getting started with AWS WAF
AWS WAF is comprised of web access control lists (web ACLs) and various rules within it. If you have not worked with web ACLs before, these give you fine-grained control over the web requests responded to by Amazon API Gateway API, Amazon CloudFront distribution, or Application Load Balancer (AWS ALB).
Here’s what the interface looks like:
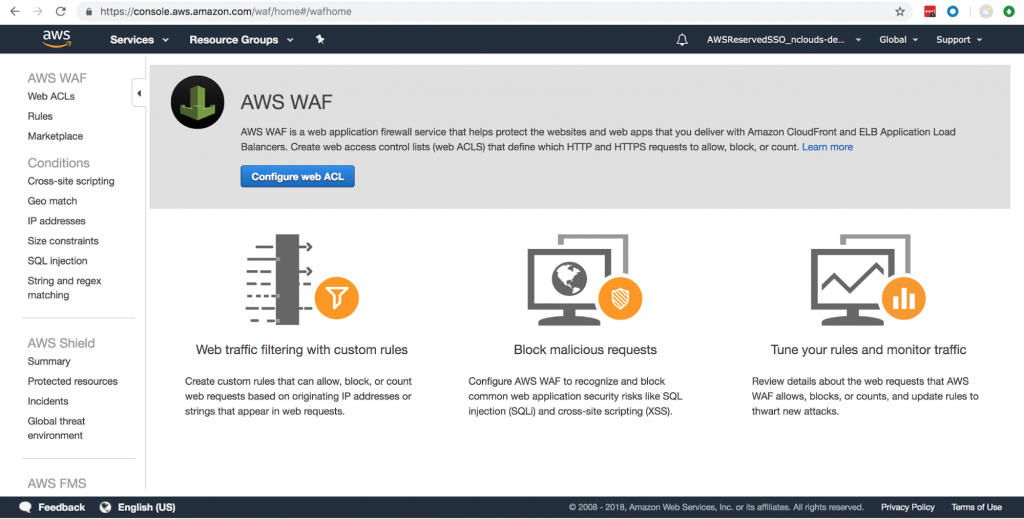
On this screen, you can create web ACLs and add or create rules in it. In the AWS Marketplace, you can find existing rules developed by trusted authorities available for use (along with pricing information). AWS WAF comes with preconfigured rules that will help you protect your app from various kinds of attacks. AWS WAF can only be applied in front of AWS Application Load Balancer (AWS ALB), Amazon CloudFront distribution, or Amazon API Gateway.
The preconfigure template documentation can be found here:
https://aws.amazon.com/answers/security/aws-waf-security-automations/?refid=gs_card
This template creates a set of resources as you can see here:
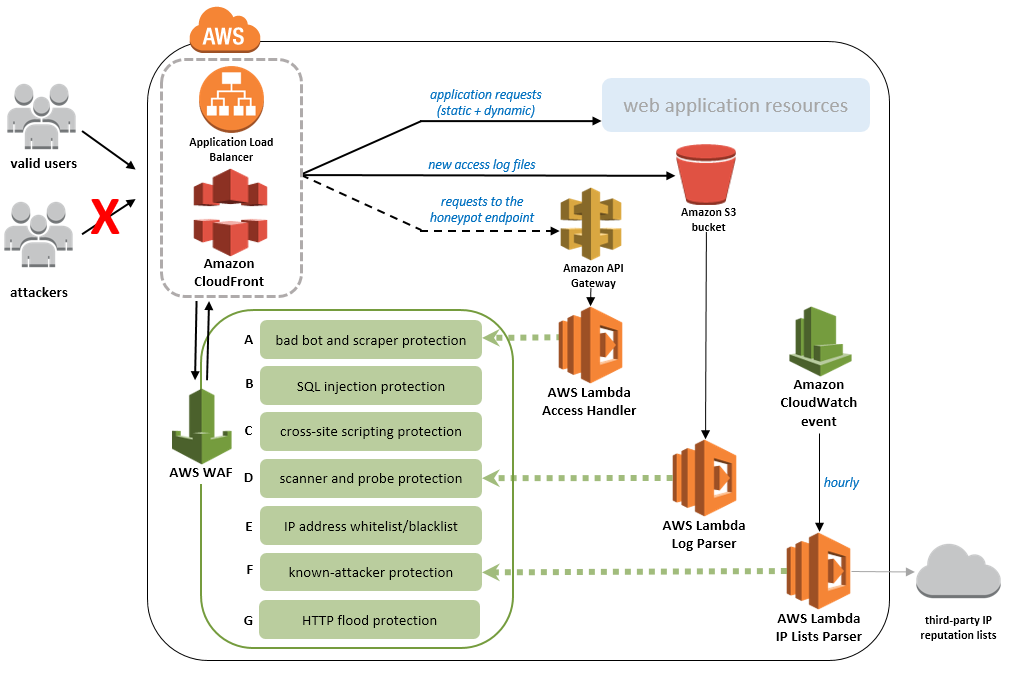
This solution is easy to deploy via AWS CloudFormation, and you can turn on and off prevention against attacks described in the above diagram.
Rules created by AWS WAF
This template created the following rules:
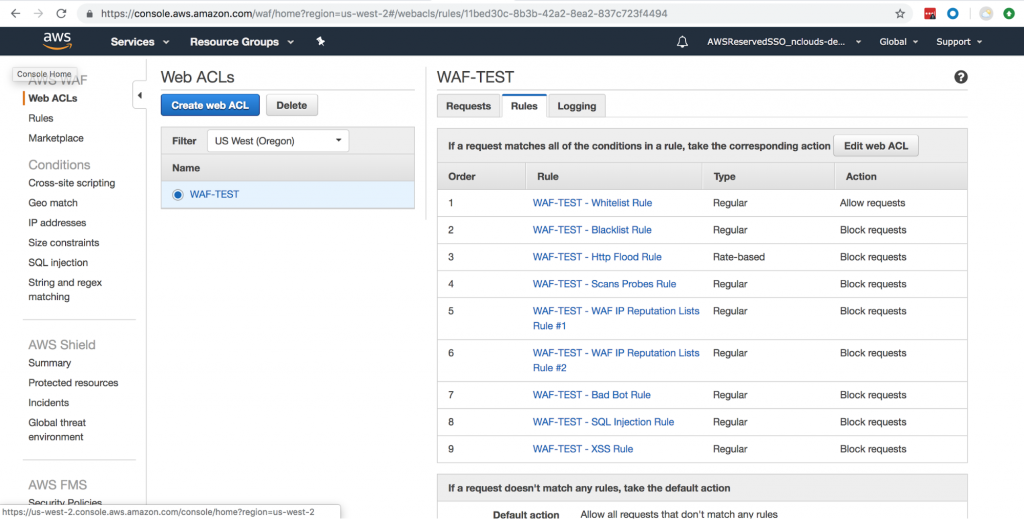
Let’s review each of the rules.
1. Bad bot & scraper protection
When you launch the AWS CloudFormation script, it will give you a honeypot URL in the output that you can embed in your web application as a hidden HTML link. So, if a bot hits that URL, that IP will get blocked and the user won’t be able to access your web application further.
2. SQL injection protection
This rule will protect your web application from SQL injection (SQLi) attacks. It will scan URLs, query string, headers, HTML body, and much more. Take a look at the rules in the following image:
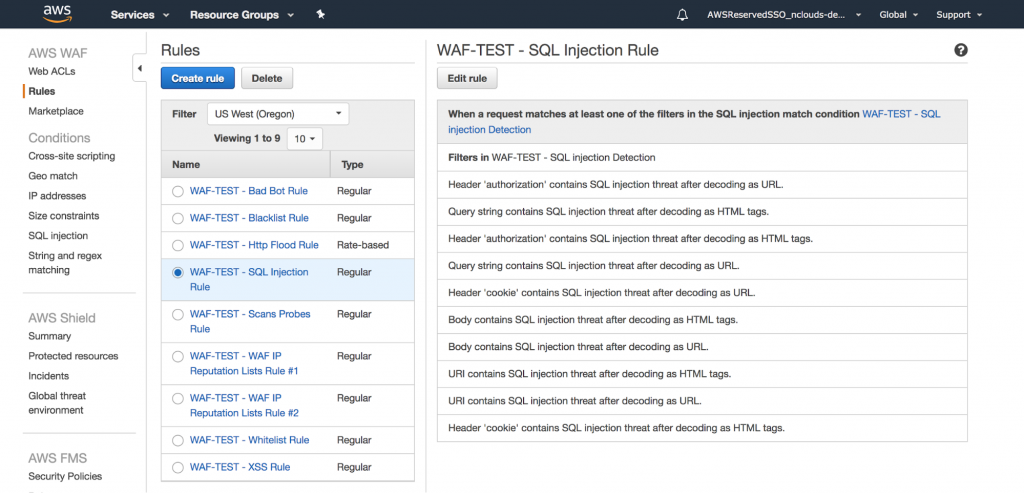
3. Cross-site scripting protection
This protection creates a rule that will protect your web application from XSS scripts. It will scan URLs, query string, headers, and HTML body. The same set of rules will be defined for XSS attacks as those defined for SQL injection.
4. Scanner & probe protection
A custom AWS Lambda function automatically parses access logs, automatically inspects for suspicious behavior, and adds that IP to a block list of IP addresses.
5. Whitelisting & blacklisting IPs
This rule allows you to manually whitelist and blacklist IP addresses.
6. Known attacker protection
A custom AWS Lambda function automatically checks third-party IP reputation lists hourly for malicious IP addresses to add to an AWS WAF block list.
7. HTTP flood protection
This component configures a rate-based rule that automatically blocks requests from a client that exceeds a certain threshold that you specified when creating the stack.
Applying web ACLs to resources
As described above, WAF can only be applied to AWS ALB, Amazon CloudFront distribution, or Amazon API Gateway. You can add web ACL association in the web ACL Rules tab as shown below:
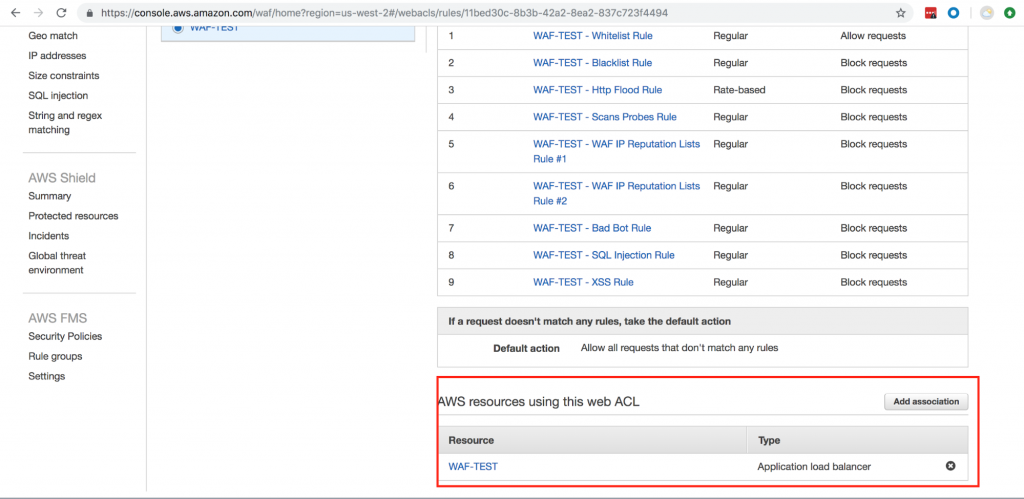
For the purposes of this demo, I have applied these rules to AWS ALB. Now, let’s see some of these rules in action.
Here is my sample Apache web server running behind AWS ALB:
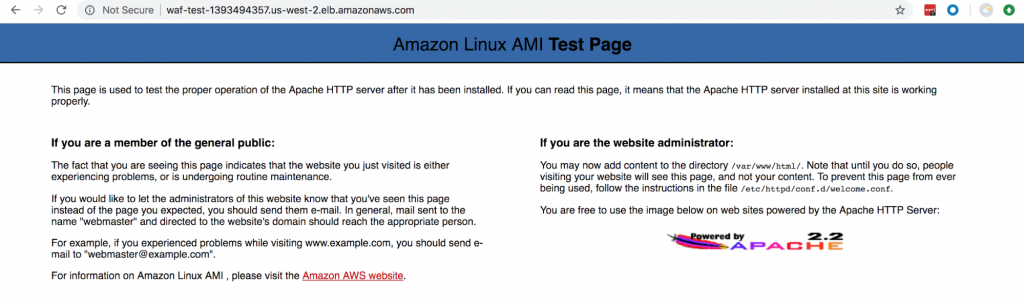
Now, let’s check the SQL injection rule. I will inject SQL in the query string.
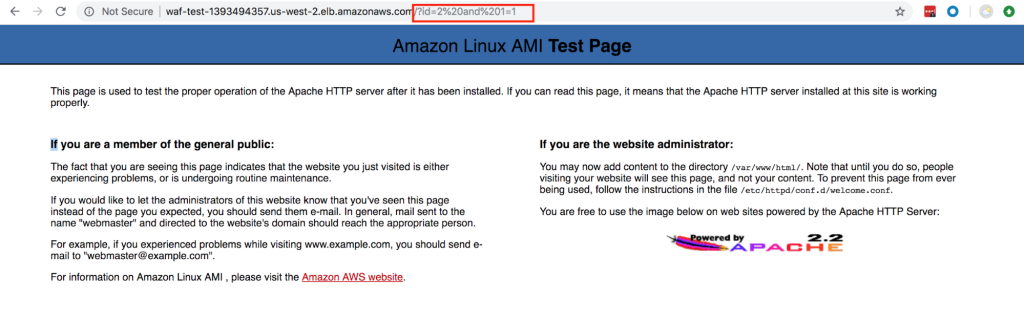
Before applying web ACL:
As shown below, prior to applying web ACL, it will allow you to pass, your site will be vulnerable, and a hacker can easily play with your database.
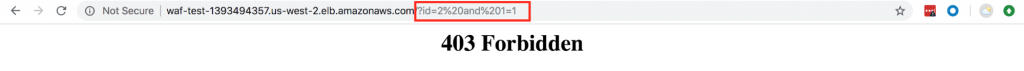
After applying ACL:
As shown below, after applying web ACL it will return a 403 Forbidden error. You can customize pages accordingly in your web app and Apache config.
Once you have designed a web ACL, you can apply it to as many applications as you want. Create it once, and you can attach it to different apps.
You can review the blocked request in the web ACL request tab in a nicely presented graph as shown below:
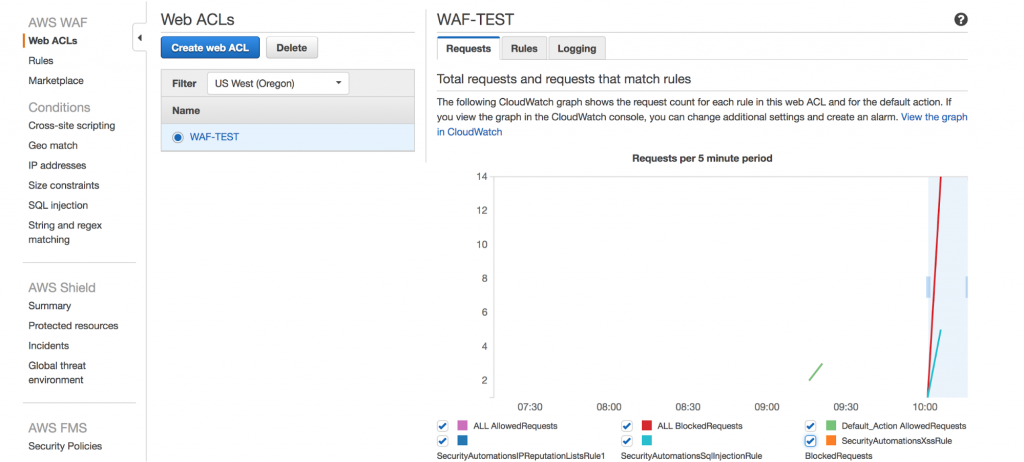
The SQL injection request that was blocked can be viewed as shown below:
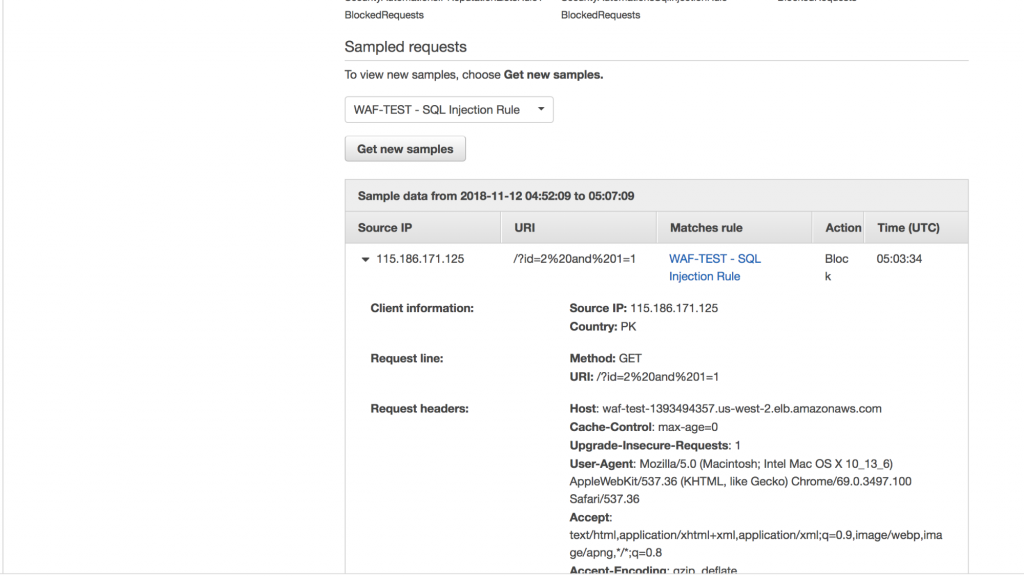
And, there’s more. You can also create different kinds of rules yourself. These rules can be based on IP, rate-based, string, and regex (regular expression) matching and geolocation, as well.
AWS Shield Standard
The ACL AWS Shield Standard comes included with AWS WAF at no cost and helps you protect from DDoS attacks. AWS Shield Advanced is available at an additional cost. You can review the standard protection and advanced protection here:
https://console.aws.amazon.com/waf/home#/ddp/onboard/info
What’s next?
AWS Web Application Firewall (AWS WAF) provides a way to protect your web applications against common exploits and threats. It’s easy to deploy and maintain, and you can add or modify rules at runtime. So, now that you’ve learned what AWS WAF is and how you can create and apply it, you can start implementing it on your production web applications. In no time you’ll have your apps secured, and you’ll be getting real-time visibility to the requests coming to your application.
The team at nClouds is here to help with your security and all your AWS infrastructure assess/plan, build, and manage requirements.


